- October 13, 2021
- Posted by: admin
- Category: BitCoin, Blockchain, Cryptocurrency, Investments
Decentralized Identifiers (DIDs) built on the immutable ledger of Bitcoin can empower users to secure their own personal data on the web.
On October 4, 2021, Facebook, along with WhatsApp and Instagram, disappeared from the internet.
Their DNS names stopped resolving, and their infrastructure IPs were offline. They were completely disconnected from the internet. At the same time, it was reported that 1.5 billion people allegedly had their personal data stolen from Facebook and posted for sale. To make matters worse, anyone who relied on Facebook to log in on third-party services was in the dark as well. The sign-in buttons we see on so many web pages are a symptom of the problem.
And if that weren’t enough, the day prior, whistleblower Frances Haugen revealed on “60 Minutes” that Facebook has long maintained a culture that “chose to optimize for its own interests” over what was good for the public.
But it doesn’t have to be this way. In recent weeks, key members of the World Wide Web Consortium (W3C), led by Mozilla, have stymied efforts to approve a web standard that would allow billions of people to privately and securely control their own data and identities. The proposal — now years in the making and mere months from the finish line — is known as Decentralized Identifiers (DIDs). These W3C members, in an egregiously opportunistic move, are protecting their own revenue streams, for themselves and for their political ideologies, at the expense of billions of people who would benefit from such a web standard. It seems Facebook is not alone in fostering a culture of putting internal business interests above the public interest.
Without proof of identity, an individual cannot access banking services, gain employment, or receive voting rights. According to the World Bank, 1.1 billion people are not able to formally prove their identity. The majority live in Africa and Asia and more than one-third are children who are unregistered. The United Nations identifies “preservation of identity” as a fundamental right of a child (Article 8 of the United Nations Convention of Rights of the Child). In Europe, the General Data Protection Regulation (GDPR) standard lacks provisions for user authentication. Identity thieves can take advantage of this oversight to steal data from data pools, leading to the rise of identity theft and online fraud. DIDs can solve all of these issues.
Corporations that own our personal data in their centralized systems have proven to be hopelessly inadequate stewards of that data. The world has seen a massive increase in identity theft, and the growth of surveillance capitalism — an entire shadow industry that analyzes, sells, and monetizes our data. In 2018, 2.8 billion consumer records were exposed through data breaches resulting in an estimated cost of more than $654 billion. The 2017 Equifax data breach exposed the personal data of more than 147 million people, affecting 56% of Americans. Recently, it was revealed that Syniverse, a company that routes billions of text messages for the largest mobile carriers, quietly disclosed that hackers were inside its systems for five years.
We should be the ones who own our IDs, not companies. As apps and corporations have become our de facto identity controllers, users do not have any control over their own identities. Between the societal and financial implications It is a moral imperative to implement the DID web standard and empower users to be able to secure their own identities. If the self-custody ethos is “not your keys, not your coins,” the ethos for DIDs is, “Not your DIDs, not your identity.”
What Are DIDs?
But, how do DIDs achieve this and what does this have to do with Bitcoin? First, we need to learn how DIDs work. DIDs are cryptographically-secured IDs that users create, own and control — independent of centralized identities. They include robustly decentralized implementations, protecting against tampering and interdiction.
DIDs are a simple, semi-human readable, syntax that describes a method and identifier.
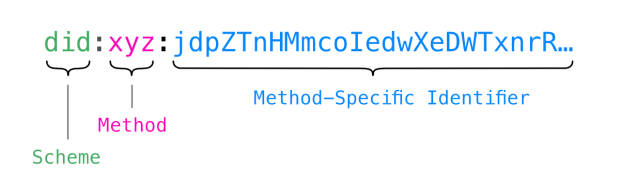
Although a DID can be used to describe something as simple as a private key, the DID identifier will often point to an address where a corresponding DID document can be found. In its simplest form, the public DID document will contain public keys and endpoints. Endpoints are destinations on the internet where our encrypted and private data lives.
By anchoring the initial DID document and any subsequent changes to the blockchain, throughout our lifetimes, we can prove the irreversible chronology of edits to our DID documents over time. In the following example, imagine you anchor a DID document to an address on the blockchain so that people can find your data when you give them your DID identifier. Occasionally, any changes you make to the document over the years (as when you get a new phone and roll over the keys) will be anchored into future blocks on that blockchain. (Fun fact: Satoshi Nakamoto’s original label for the Bitcoin blockchain was a “timechain.”)
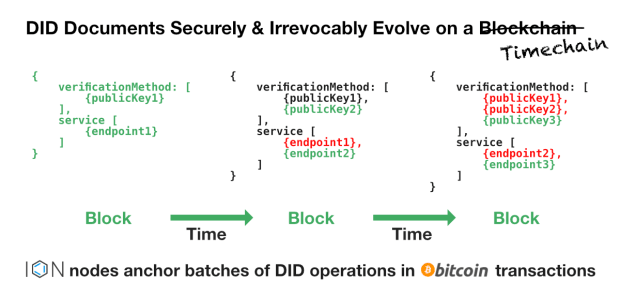
Blockchains are not technically required for DIDs. However, DID documents ideally reside within a framework that robustly solves the Chronological Oracle Problem, and is accessible to third parties in a tamper-proof manner that the individual owner can fully control. The most secure and most censor-resistant open blockchains, like Bitcoin, are ideal systems for anchoring DID documents, since blockchains are a decentralized, immutable and chronological event record that the entirety of humanity can agree on. The blockchain attests to the ordering of events, and proof of work is what ties that to our perception of time.
In other words, you can publish new changes to your DID document, over a lifetime, and the blockchain ensures that everyone can agree that the document is accurate and up to date. Think of it like a Google Doc that no central authority controls. A system like this needs to outlast every company, and provide a service that can last for a lifetime, or more. Thus, the more robustly decentralized, secure and long-lasting the blockchain, the better. There is no better choice for securing DIDs than Bitcoin — everything else is a risky experiment.
Not Just For Logins
And DIDs aren’t only for logins. We can attach these identifiers to anything in the virtual world.
Imagine a future where DIDs are attached to everything, such as any Schema.org object — the agreed-upon standard for common semantic data. These objects define practically everything we interact with in cyberspace: grocery lists, music playlists, videos, block quotes, blog posts, news, events, organizations, products, reviews, places and so on. The lists of things DIDs can be applied to are practically endless.
DIDs are ideal for organizations issuing “Verifiable Credentials” to user DIDs such as digital diplomas, proof of employment, licenses, deeds for property, bar certifications, notarization, etc. The organizations maintain their own DIDs and issue the Verifiable Credentials to the DIDs that users create on their own — that way, every institution and individual is completely in charge of creating and sharing their own identities. Each user might have many different DIDs, for all sorts of personas.
There are many different DID methods and projects for each of these methods. Below, we’ll examine the ION method, which is an open network that uses Bitcoin for chronologically-securing DIDs. Microsoft contributes to ION’s public development through the Decentralized Identity Foundation (DIF), as do many other entities that want to become the leaders for issuing and managing Verifiable Credentials. Neither Microsoft nor any other single entity controls ION.
ION And Bitcoin
ION is an open, public, permissionless Layer 2 Decentralized Identifier network that runs atop Bitcoin to enable robustly decentralized, interdiction-resistant W3C DIDs at scale. Unlike other DID protocols, ION is a purely deterministic sidetree protocol, which requires no special tokens, trusted validators, or additional consensus mechanisms; the linear progression of Bitcoin’s timechain is all that’s required for its operation.
ION settled on Bitcoin as its blockchain of choice, since Bitcoin is the most secure, most decentralized and most censor-resistant blockchain. Bitcoin is the one and only timechain.
“So, for us, Bitcoin was a necessary condition for success. The reason it wasn’t a super hard sell was that it was something we had to have and we knew we couldn’t own it. We wanted something that was differentiated and decentralized — because otherwise we could do this with a database like Azure… With Bitcoin, one of the biggest elements of this — and this did take some understanding — was security. All of those other use cases being possible is actually a symptom of no one controlling it. What we really made our decision based on was the decentralized nature plus the security. It’s the cost of attack and how you order transactions that’s important. When we started crunching the numbers, we realized that Bitcoin was the only chain that would probably be too costly to attack.“ –Daniel Buchner, Microsoft Decentralized Identity
ION is a privacy-preserving framework. All DIDs are public, similar to the way the world wide web’s Domain Name System (DNS) is public. Yet, DIDs hold no personal data. ION only cares about documenting encryption keys and routing endpoints. DIDs are not assigned to individuals by a third party. Instead, users create their own DIDs and sign operations from their own private wallet to emit them either directly to the Bitcoin blockchain or to an ION node which will efficiently batch many of the encrypted operations into a single Bitcoin block transaction.
A single Bitcoin transaction could, in theory, batch millions of ION operations. This alone invalidates the fallacious and disingenuous argument that a single Bitcoin transaction is supposedly inefficient. Nothing could be further from the truth.
ION nodes observe each new block on the Bitcoin blockchain, for new ION operations, to stay in sync. There is no need for consensus between ION nodes — it’s purely data-deterministic based on the latest state of the Bitcoin blockchain.
ION is built to scale to support the entire globe. It’s batching operation can process thousands of DIDs per second, tens of billions of operations annually. Even if, someday, the cost of a single Bitcoin transaction were to rise to $100, each DID update would cost a user roughly 1 cent, with the average user perhaps doing 100 of these operations in a year. Such operations are infrequent in daily practice, for example, rolling private keys from an old phone to a new phone.
ION can support the entire globe with over 50 billion DID operations per year. Although not a requirement, anyone could run an ION node with a Raspberry Pi and a very large hard drive. The drive can even be pruned to 4% of total data.
Verifiable Credentials
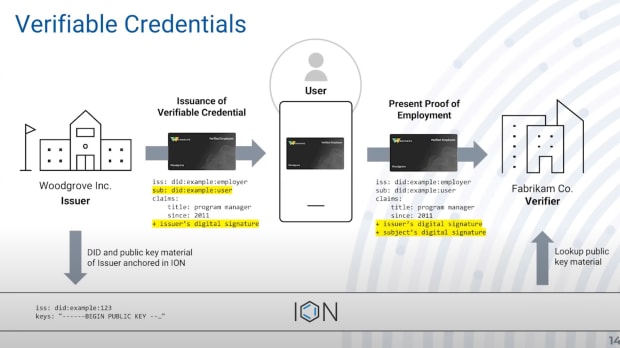
The very foundation of Verifiable Credentials is the ability to sign a proof from someone to someone else. For instance, your employer might use its DID to sign employment credentials to its employees’ DIDs and the employees can go anywhere and prove that they, in fact, are employed by the company.
In this case, ION is just used to look up the public keys behind the IDs and do the signing. The employee’s and employer’s verifiable credentials are then made available for others to verify, when permission is granted by the user.
Understandably, people might be concerned about how this technology could be used by governments. DIDs on their own are relatively pure. The alarming part is in how authoritarian entities might issue credentials from their own centralized servers. However, credentials can just as easily be attached to centralized or federated IDs that offer us no control whatsoever.
The fact that DIDs can act as a conduit for potentially unjust credentials is entirely orthogonal. DIDs are created by users and the verifiable credentials that users add to their own DIDs are issued from centralized entities that can be torn down.
It can be helpful to think of identity as clothing. Today, centralized entities force us to wear the clothing they issue us in their online prisons. DIDs are clothes that we sew ourselves and independently choose to wear for our different personas. DID wardrobes are flexible — we can choose to wear pseudonymous invisibility cloaks if we wish. As long as we retain our private keys, no one else can wear our clothing. Verifiable credentials are the badges, or scarlet letters, that society coerces us to attach to certain types of clothing. Badges we wear on our clothes can serve as part of a trust network or can be coercive. The timechain is the incorruptible DNS-like ledger that we use to communicate where our clothes can be seen.
The coercion to attach badges or scarlet letters to our clothing is another name for society — this happens with or without DIDs. Bitcoin helps us build better and more just societies, while DIDs act as an identity layer within those societies.
DIDs + Identity Hubs = The Semantic Web
DID documents can point to routing endpoints — places where your data is securely stored. The DIF Secure Data Storage Working Group has a project developing personal data stores or “Identity Hubs” which are private servers where users will keep an encrypted vault of their personal data.
Companies like Umbrel are positioned to be the home Identity Hub providers of the future. For those unable or unwilling to own their own data, trusted third parties could provide data custodial services. The self-custody ethos still applies here: “Not your server, not your data.”
DIDs are all public, just like DNS domains. Individuals or services can go to anyone’s Hub and ask it questions, and the user controls who gets access. A developer could build a crawler to every DID and look for secondhand product objects and render a client-side UI that looks a lot like Craigslist.
The identity web is the semantic web that the world always wanted. There’s no need for crawling web pages in a DID-based world. Apps or users can cURL the data of any business or any person, and prove all sorts of things from trusted parties. This makes the semantic web accessible between peers and businesses alike. Below, we’ll explore different use cases for this semantic web:
Messaging
With DID Communications, otherwise known as DIDComm, Decentralized Identifiers plus Identity Hubs provide a DID-encrypted data storage and messaging layer that can replace one-off protocols (e.g., Signal) with a universal standard for encrypted communications between peers.
If you know someone’s DID, you can look up their routing endpoint, look up their public key, and send them an encrypted message, without an intermediary, and that message can land in their private data store where they can read it in a client-side messaging app. This means developers can build apps, like Signal or Telegram, on a standardized infrastructure where the app is mostly UI with some affordances built around it. DIDComm can’t be censored or deplatformed. Users are given complete control of their interactions. It is plausible that Twitter could incorporate DIDs and Identity Hubs for its Bluesky project.
While Bitcoin Lightning apps, like Sphinx, are becoming popular for messaging, DIDComm is a more robust solution. Instead of sending messages with an elaborate Lightning apparatus that piggybacks infrastructure ill-equipped for app traffic, it’s easier to use a standard encrypted layer that’s actually designed for application traffic. And while Lightning is an amazing, life-changing technology for transferring money, it’s less than ideal to attach messaging to transaction infrastructure that fundamentally cannot handle all the things it needs to. Additionally, Lightning requires you to always have a Lightning node online, to resolve lookups, which isn’t required with DIDComm.
Accreditation
Many activities in our world require the establishment of trust between participants. DIDs plus Identity Hubs allow individuals, organizations and companies to publicly post credentials that others can discover and independently verify. For example, if you want to verify that a school is accredited, you can resolve a school’s DID and use it to fetch credential objects, such as an accreditation, from that school’s hub.
Travel
Today, your preferences, tickets, reservations and other travel data is strewn across hundreds of different hotel, airline and travel apps in a massive and unworkable mess. DIDs and Identity Hubs can help unify these app experiences.
Imagine you grant your hotel the ability to view and edit your trip object. You grant your rental car agency the ability to view and edit that same trip object and it is able to receive and react to the updates that you or your hotel makes to the trip. Your hub tracks all of the updates and you can visualize the trip with an app that is mostly client-side and UI-based. Your Identity Hub acts as a personal server, replacing the need for surveillance capitalism and travel aggregation services like Google.
Preventing Deep Fakes
Celebrities or politicians can issue DIDs and sign any text or video and add their signature for others to verify.
For example, if a web browser supported DIDs, a user could hover over content and see the signature and verify the origin of the content. This could, in theory, solve the problem of deep fakes. As long as any content is signed with a DID, it is possible to verify the source of that content. DID signatures can act as a proof conduit for anything.
Social Unrest
Frances Haugen recounted in her time with Facebook that she saw, “conflicts of interest between what was good for the public and what was good for Facebook.” This included amplifying hate, misinformation and political unrest.
While DIDs cannot solve all of the problems of the world, it can reduce misinformation through verifiable and trusted data signatures on any shared content. DIDs can help us identify the difference between bots intentionally deployed to sow misinformation and real humans who have good standing in their communities.
When users own their own data, surveillance capitalist corporations like Facebook would have a more difficult time manipulating our own character flaws and judgement. This in turn can help support the W3C’s own goal of fostering healthy communities and debate, while making it much more difficult for social networks and political parties to amplify hate, misinformation and social unrest.
Spam
Businesses and consumers experience costs of almost $20 billion annually due to email spam, in the U.S. alone. DIDs can solve any kind of spam, whether they be spam from phones, emails, text messages and so on.
Lightning apps like Sphinx propose fighting spam with very low fees, in hopes that it becomes too expensive for spammers to use in bulk. DIDs offer a superior solution by allowing users of any communications media to require senders to assert Verifiable Credentials with accreditations from trusted third parties.
For example, a user can choose to automatically mark any communications as spam unless they have DIDs that contain a matching ServiceChannel, ContactPoint or any custom Intangible and are in good standing with family, friends, the Better Business Bureau (BBB), AARP or their local chamber of commerce. DIDs would also allow services to trust users and obviate the need for those stupid “are you human?” tests to prove that you’re not a robot.
Phishing And Online Fraud
According to the FBI, Business Email Compromise (BEC) is an elaborate scam targeting businesses working with foreign suppliers and/or businesses regularly performing wire transfer payments. Email Account Compromise (EAC) is a similar scam that targets individuals. Fraudsters compromise email accounts through social engineering, phishing or computer intrusion techniques to conduct unauthorized transfer of funds. These scams cost businesses and individuals billions of dollars in losses per year.
Much of these crimes could be avoided with DIDs, which move authentications away from fallible passwords and into private keys embedded in hardware elements that are inseparable from devices, unless reconstructed through recombination of seed material that is nearly impossible for outsiders to reproduce.
Music Streaming
With DIDs and Identity Hubs, you could share your favorite music playlists between multiple music streaming services, friends or family. Instead of services each owning all of your playlists and keeping them in their walled gardens, you would store the playlist object on your personal server and grant access to different services.
New Business Models
Companies that would be disrupted by DIDs can explore new business models that provide novel services to users who are now in control of their own data. These companies can act as custodians to encrypted user data, where the user can still decide who can see what. In a world where DIDs are commonplace, corporations will need to ask permission for data and users will ideally choose to use client-side UIs that prevent data capture by those companies.
Companies can also find innovative ways to help users manage their private keys. After all, in a world of decentralized, user-owned DIDs, there is no “Forgot Password” button. Instead, users can rely on trusted custodians to manage their keys.
Companies can also create new ways for users to recreate lost keys from multiple factors and fuzzy recombination. Imagine being able to elect trusted guardians who can independently help you recreate a lost DID with a few clicks. In the event of a catastrophic loss, you can create new DIDs and independently reassociate them with verifiable credentials.
Web Browsers And The War Against DIDs
As one might imagine, corporations that make their money off of owning our identities are building up strawmen in order to prevent the standardization of DIDs in web browsers. While the W3C DID Proposed Recommendation does not technically require web browsers, DIDs would require browser integration to really shine.
For example, having a built-in wallet to manage DIDs/keys for your personas, and a UI that helps you pick which to use for which interactions, would make DIDs much easier to use. Secondly, you would want DID URLs to work in your browser’s URL bar, so that it quickly loads DID-relative content that the URL specifies, such as social posts from the personal data store associated with the DID, or importing a verified DID into your contacts.
Finally, you would want other DID-based APIs in the browser, like DIDComm messaging, which would allow any website to instantly enable users to privately message in their app without requiring any backend for the site to setup or manage.
The browser understanding DIDs, as a result of DIDs existing, is very much a goal. W3C members should put aside their cherished business models and seriously consider supporting web DIDs to help ensure personal privacy, identity and basic identity-based human rights.
What Bitcoin DID
Some W3C members, such as Mozilla and Google, have publicly opposed DIDs in web browsers. Reasons include some debatable technical concerns, but some have also voiced environmental concerns since DIDs elevate proof-of-work consensus methods used by Bitcoin. This argument is a bit like refusing to build a pipe factory because some of those pipes might be used for transporting fossil fuels, even though those pipes would be enormously beneficial to humanity. However, DIDs do not require the use of Bitcoin. Bitcoin just happens to be the world’s best “truth machine.”
Bitcoin’s energy consumption is wildly exaggerated in the media and appears to be used as a strawman by W3C member organizations who are resisting disruption to their business models. Blocking DIDs from becoming a standard in web browsers would undermine every W3C ethical web principle. The energy usage argument regarding proof of work for DIDs simply does not hold merit.
Proof of work is the only battle-tested and proven secure consensus method for blockchains. Alternative consensus methods, such as proof of stake, are still experimental, rely on human behavior, have known issues, can centralize over time and can fail to produce irrefutable history. The link between proof of work, time and heat is fundamental: an incorruptible distinction between past and future is impossible without heat.
For the expense of roughly 0.1% of total global emissions, or a small fraction of the energy spent on clothes dryers, Bitcoin provides the most secure global chronological information and monetary settlement layer while incentivizing renewable energy. Standby devices in the U.S. alone use more than twice as much energy as does all proof-of-work mining. The <video> tag in the HTML spec is directly responsible for orders of magnitude more energy usage than all proof-of-work mining, for less benefit — entertainment versus securing a base layer for decentralized property and identity.
Blocking web DIDs would be akin to blocking HTML on the basis that corporate data centers consume 1% of global electricity. Bitcoin’s share of 0.09% of global energy consumption (0.44% of global electricity consumption) is a rounding error, and its energy is sourced from a greater share of renewables than any industry on the planet. Furthermore, Bitcoin turns energy producers into technology companies — increasing revenue per kilowatt hour and acting as a shock absorber for the renewable energy sector, in a portable manner. As a tool to empower billions of people to obtain verifiable identity, employment, banking, voting rights and hundreds of billions of dollars in fraud protection, DIDs alone would be worth the relatively minimal negative externalities of proof of work.
If you believe the web should not cause harm to society, if you believe that the web is for all people and must support healthy community and debate, if you believe security and privacy are essential and that the web must enable freedom of expression while making it possible for people to verify the information they see, if you believe the web must be transparent and enhance individuals’ control and power, and if you believe people should be able to render web content as they want, then you must support an effort to bring DIDs to web browsers and the world wide web. The moral imperative is too great to ignore.
The world needs an internet that affords users the identity and data autonomy they need and deserve. And for the equivalent energy spent on Christmas lights, we can empower users across the globe and move humanity forward for the better.
This is a guest post by Level39. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
